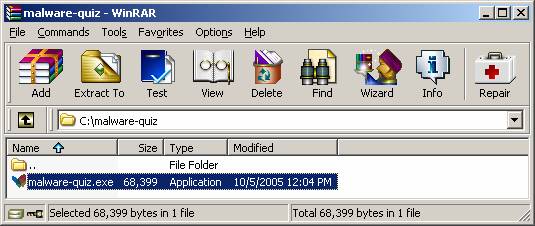
Malware Analysis:
Quiz 2
Submitted by:
Jack McCarthy
TD Waterhouse
jackmccarthy -AT- (\tdwaterhouse & com
October 14, 2005
|
Introduction Pedro
Bueno, one of the incident handlers at the SANS ISC (Internet Storm Center),
has begun an interesting little side-project regarding malware analysis. His personal Handler’s Page is focused on
providing a new Malware Analysis Challenge every couple of weeks, where
anyone who is interested may attempt this challenge. There is usually a two-week time limit in
which all answers can be submitted and at the end of this two-week period,
the official answers are posted along with the names of the people who
submitted correct answers. The current
challenge, “Malware Analysis Quiz 2”, involves
downloading the file
malware-quiz.exe, analyzing it and answering the
associated questions. This is my
submission to Pedro’s Malware Analysis Quiz: Part 2. Downloading the suspect file The first step is to download the file
malware-quiz.exe and check its MD5 hash value.
This process will verify that we are working with the correct file (the
one Pedro intended for us to work with) and not some altered version. [See
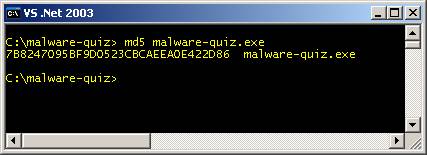
the tools section for more information on the MD5 tool that was used.] Running the
following command will generate the MD5 hash value for the file I just
downloaded:
Fig. 1 Pedro’s hash value: 7b8247095bf9d0523cbcaeea0e422d86
malware-quiz.exe My hash value: 7B8247095BF9D0523CBCAEEA0E422D86 malware-quiz.exe Great, the hash values match, confirming that we are in fact
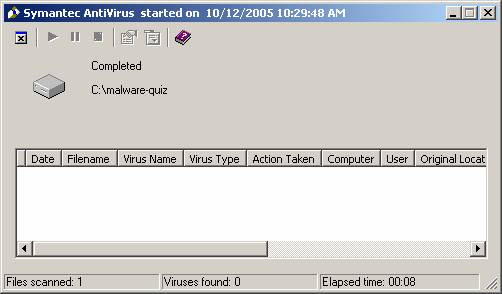
working with the intended file. Virus Scan As an
added precaution for this exercise, I scanned the file with Symantec
Corporate AV 8.1 with 10/11/05 virus definitions. SAV 8.1 does not view this file as a threat,
so it’s safe to work with. [See the tools section for more information on
SAV Corporate 8.1.] [Under
typical malware analysis conditions (if there is such a thing), you would be
working on an isolated machine/network/VMWare, giving the malware free reign
to do what it wants. This way you are
not restricting the malware in any way and can accurately observe and record
all of its actions.]
Fig.
2 Question and Answer Section Part I: Short
Answers 1) “Is this file packed? If so,
which packer was used?” Yes,
this file is packed. Both UPX and
WinRAR were used in the creation of this file,
malware-quiz.exe. 2) “Which command did you use to
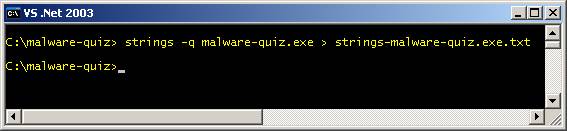
identify it?” Using
the command-line utility ‘Strings’ from Sysinternals: strings
–q malware-quiz.exe > strings-malware-quiz.exe.txt 3) “Do you believe that is there
any other way to identify the packer?” Yes, you
could open the file using a hex editor and view the ASCII strings. 3a) “Please describe the
directory which this file will be installed?” c:\windows\temp 4) “In the process to unpack
this file, please describe all the options that you saw. And by 'describe' I
mean tell me what does it do when unpacking or not...” No
options, screen prompts or windows were visible when unpacking (double
clicking and running) the file. It
gives no indication that any action was performed. 5) “What does this malware do?” When
you double click and run the file
malware-quiz.exe, it silently extracts its
embedded file malware.exe to the pre-determined
destination folder of c:\windows\temp.
When you run the file malware.exe from a command prompt, it will
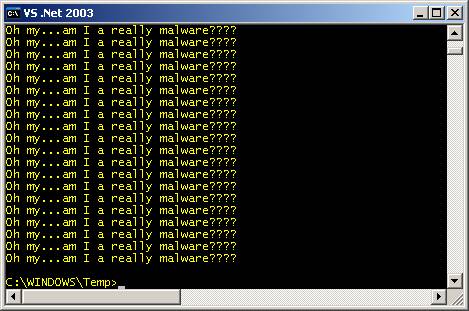
print the following line onto the screen 99 times: Oh my...am I a really malware???? 6) “And finally, as a bonus
question: What is the meaning of life?” The
number ‘42’. Part II: Long Answers 1) “Is this file packed? If so,
which packer was used?” Yes,
this file is packed. Both UPX and
WinRAR were used in the creation of this file,
malware-quiz.exe. 2) “Which command did you use to
identify it?” & 3) “Do you believe that is there
any other way to identify the packer?” [I
combined my answers for questions 2 & 3 and answered them as one. The
reason I did this is because I used several different methods when analyzing
this file and figured it made more sense to just combine the two of them into
one explanation.] Initial Identification The
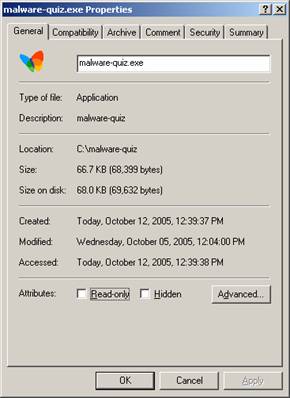
first thing I did was I performed a visual inspection of the file and its
properties. Taking a look at file
properties like file name, size, MAC times (modified, accessed, created) and
summary will give you a ‘starting point’ as to the type of a file you are
preparing to analyze. [This
visual inspection process is meant to be viewed as a ‘first glance’ approach
only, not as an absolute. Don’t assume
anything just because the file has an innocent name and a pretty little
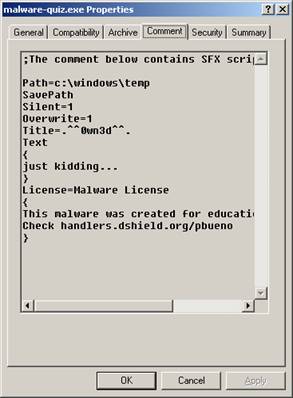
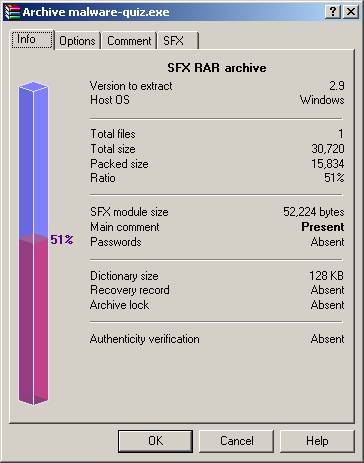
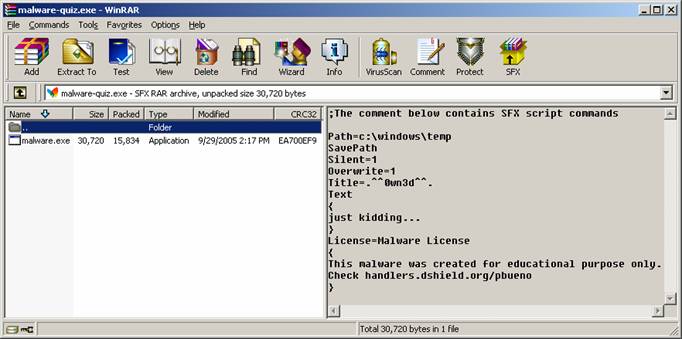
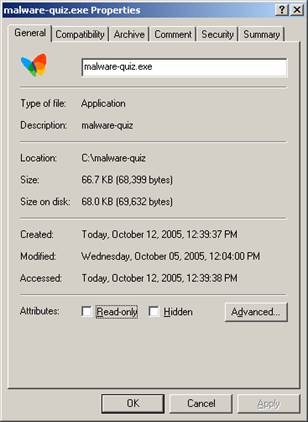
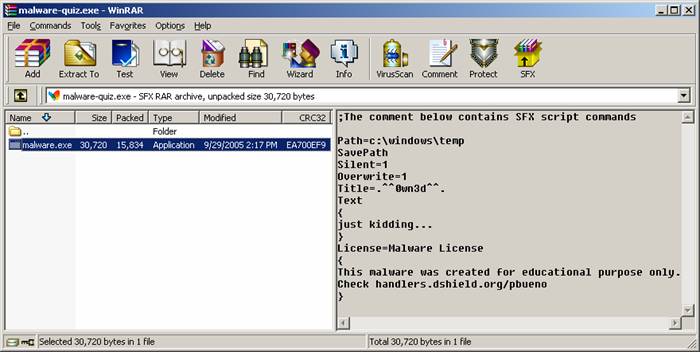
butterfly icon.] Already having WinRAR installed on my computer gave me an advantage in viewing the properties of the file. WinRAR automatically recognizes that malware-quiz.exe is a WinRAR SFX (SelF eXtracting) archive file and displays the additional property tabs ‘Archive’ and ‘Comment’. If I didn’t have WinRAR installed, these additional property tabs would not be displayed.
Fig.
3 Fig. 4
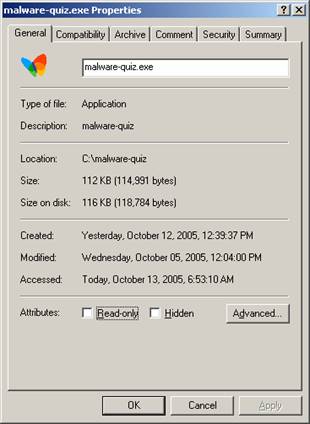
Fig.
5 After
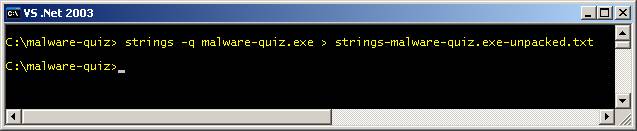
the visual inspection, the command-line utility ‘Strings’ from Sysinternals
was run against the file. [See the tools section for more information on
Strings.] [When
you run this utility, make sure you redirect the output to a text file for
better viewing.]
Fig.
6 The
purpose of doing this is to get a quick view of any embedded ASCII and
UNICODE strings (characters, words and/or phrases) that may be contained
inside this file. Analyzing the output
can give us clues as to the different characteristics and composition of the
file. [The
flag ‘-q’ is for ‘quiet’, meaning that it won’t print out the banner
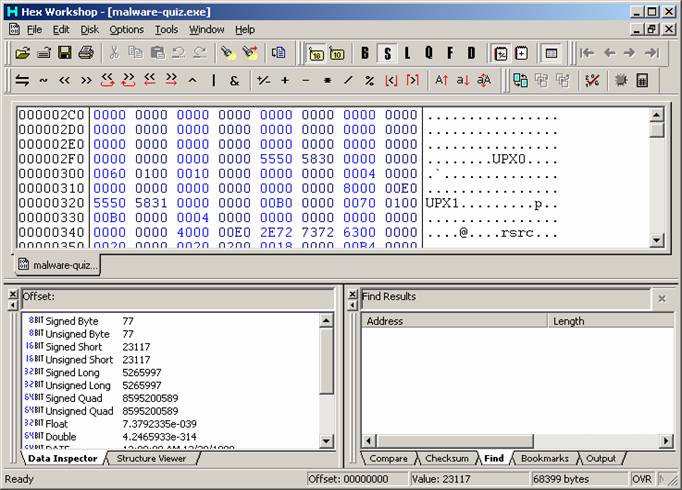
information of the utility.] When examining the output file, the first thing you notice are the strings ‘UPX0’, ‘UPX1’, ‘UPX!’. This leads you to believe that this file was packed with UPX.
Fig.
7 And the
‘WinRAR’ strings towards the
bottom of the output file would lead you to believe that the file was also
archived with WinRAR.
Fig.
8 This
clearly indicates that this file
malware-quiz.exe has the characteristics of both
WinRAR and UPX. Side note: The output from Strings is a little odd. When scanning through this output file, you
notice that there is only one line that contains the ‘WinRAR’ string. I know that when you run Strings against a
file that has been archived by WinRAR, there are a few more references to
‘WinRAR’ in the Strings output, more than what we find here. You will usually find strings such as
‘RarSFX’ and ‘Software\WinRAR SFX’, but that’s not the case here. It’s like those additional references have
been stripped out. Wonder if WinRAR
was run first and then UPX was used to compress the file to a smaller size. Initial Identification Method #2 An
additional way to initially identify this file would be to open it in a hex
editor like Hex Workshop. Using this
method, you would be able to view the same character strings as you did when
you ran the utility Strings against the file.
The output is not as neat as it is when using the utility Strings, but
it will still give you the ability to view the ASCII character strings. [See
the tools section for more information on
Hex Workshop.]
Fig.
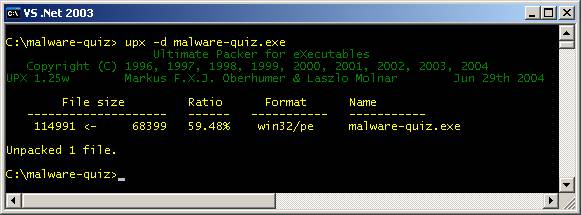
9 UPX Identification Method A way
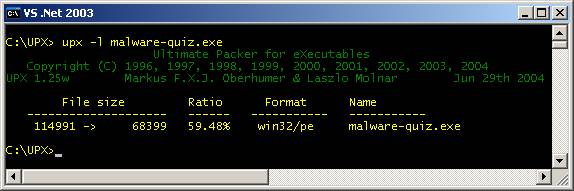
to check if the file was packed with UPX is to run the UPX command with the
–l flag (that’s a lower case ‘L’) to test the file. If the file was packed by UPX, it would
display the compression details including the file size (before & after
compression), compression ratio, file format and the name of the file. See Fig. 10. [See
the tools section for more information on UPX.]
Fig.
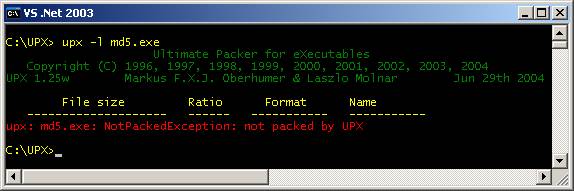
10 If the
file was not packed by UPX, it would display an error message stating that
the file was not packed by UPX. See
Fig. 11.
Fig.
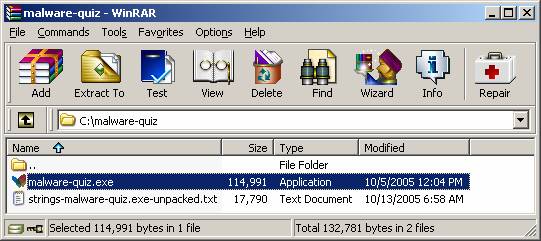
11 WinRAR Identification Method Start
up the WinRAR application; click ‘Browse for folder’ under the ‘File’ menu
and browse to the location of the file. [See
the tools section for more information on
WinRAR.]
Fig.
12 With
the file highlighted, clicking on the ‘Info’ button will display the
following information:
Fig.
13 And
clicking on the ‘View’ button will display the following information:
Fig.
14 Notice
that it gives you information on the embedded file, malware.exe, and the right windowpane lists the different options
that were used during the WinRAR archiving process. What we know so far…
·
From the strings output, the file appears to have characteristics of
both WinRAR and UPX.
·
Using the application WinRAR to view the file properties, gives us a
strong indication that WinRAR was used to archive this file. Normally, when you run Strings against a
file that has been archived with WinRAR, you will usually find multiple
references to ‘WinRAR’ in the strings output file. In this case we only find one reference,
leading me to believe that the file was packed (compressed), stripping out
those additional references.
·
Running UPX –l (lower case ‘L’) to check for compression, verifies
that the file
malware-quiz.exe was in fact packed by UPX.
Step 1 Let’s
first start off by unpacking the file with the following command:
Fig.
15 Step 2 Now
that we have the file unpacked, let’s compare how the file size changes from
before unpacking to after unpacking:
Fig.
16 – Before unpacking Fig.
17 - After unpacking Notice
the difference in the before and after sizes. Step 3 Let’s
run the command-line utility Strings against the unpacked version of the file
and analyze the output:
Fig.
18 Notice
how this Strings
output shows that there are a
few more line entries of the character strings ‘WinRAR’, where as the Strings
output for the packed file only showed one line. Also notice that since we have unpacked the
file using UPX, there is no longer any mention of UPX in the Strings output. Step4 Using
the application WinRAR, let’s take a look at the file properties of this
unpacked file. It is clear that it is
a WinRAR SFX (SelF eXtracting) archive file that contains an embedded file named malware.exe.
Fig.
19
Fig.
20 What we know up to this point… ·
The original
file, malware-quiz.exe is a WinRAR
SFX archived file that has been packed using UPX in order to decrease its
file size. When it comes to malware,
smaller is better. ·
When unpacking
the file using UPX, the file size goes from 67k to 113k. ·
When analyzing
the Strings output of the unpacked file, it now displays a ‘more normal’
resemblance of a WinRAR SFX archive file, as compared to the stripped version
we saw from the packed file. Also
notice that since we have unpacked the file using UPX, there is no longer any
mention of UPX in the Strings output. This further confirms our theory
that WinRAR was used first and then packed by UPX. ·
When viewing
the file properties through the WinRAR application, we know that this file, malware-quiz.exe contains an embedded
file named malware.exe. ·
We are now at
the point where we can extract this embedded file and continue our analysis. Step 5 We now
have a few different methods we could use to extract this embedded file:
For the
purposes of this exercise I chose to double click on it and run it. [It’s
the more ‘user-like’ thing to do.] Step 6 Now
that we have extracted the embedded file, we can continue on to the next
question. 3a) “Please describe the
directory which this file will be installed?” When
double clicking and executing the file
malware-quiz.exe, the contents of this file
(embedded file malware.exe) will get extracted and
installed to the directory c:\windows\temp. This is
an option that was most likely configured during the process of archiving the
file using WinRAR. See the screen shot
in Fig. 21. [Note:
If you were to manually extract the contents using WinRAR, you would be able
to choose your own installation directory and bypass the default setting.]
Fig.
21 How
did you determine this and come to this conclusion? When
viewing the file properties, the ‘Comment’ tab indicates the directory path
where the file will be automatically installed. Wanting to further verify this, I tested it
by clearing out the c:\windows\temp directory and then executing the file
malware-quiz.exe. Rechecking the c:\windows\temp directory,
it now contains the file malware.exe. 4) “In the process to unpack this
file, please describe all the options that you saw. And by 'describe' I mean
tell me what does it do when unpacking or not...” No
options, screen prompts or windows were displayed when double clicking and
running the file. This un-archiving
(extracting) occurred silently, giving no indication that any actions were
performed. This ‘silent’ option was
most likely configured during the archiving process using WinRAR. See the screen shot in Fig. 22.
Fig. 22 5) “What does this malware do?” When
you double click and run the file
malware-quiz.exe, it silently extracts its
embedded file malware.exe to the pre-determined
destination folder of c:\windows\temp.
When you run malware.exe from a command prompt, it will
print the following line onto the screen 99 times: Oh my...am I a really malware????
Fig.
23 When
running malware.exe from the command line, you
could redirect the output to a text
file for better analysis.
Fig.
24 Also,
if you were to double click and run the file malware.exe from Windows Explorer (instead of
running it from the command prompt), a command prompt window would open up on
your screen, print that line 99 times and then close that command prompt
window. Depending on how fast your computer is, you would most likely just
see a command prompt window flash on your screen. 6) “And finally, as a bonus
question: What is the meaning of life?” The
number ‘42’. This answer can be
found when viewing the ASCII character strings from the file malware.exe. This can be accomplished
by opening the file in Hex Workshop (see Fig. 25) or running Strings against
the file and viewing its
output (see Fig. 26).
Fig.
25
Fig.
26
Additional Analysis Section Creating a SelF eXtracting (SFX) Archive File Using WinRAR Click here to view a more detailed 'step-by-step' process of how the file malware.exe was most likely archived using WinRAR.
Using Dumpbin.exe to view both EXE files. [See
the tools section for more information on
Dumpbin.exe.]
malware-quiz.exe dumpbin output.
malware.exe dumpbin output.
Further analyzing the file malware.exe.
Initial thoughts when looking at the
output that
malware.exe generates, were that it reminds of a typical “Hello World”
C/C++ program with the text modified and set to loop 99 times. Looking at
the Strings
output,
one of the first lines towards the top mentions “Open Watcom”. This leads
me to believe that the Open Watcom C/C++ compiler was used to compile the
source code. [See
the tools section for more information on the
Open Watcom C/C++
compiler.]
Creating my own version of malware.exe Click here to view how I created my own version of malware.exe using the Open Watcom compiler and how its Strings output compares to Pedro's file.
The next step is to...
Tools Section Tool Name: Microsoft
Windows XP SP2 Price: $$$$ Link to Resource: http://www.microsoft.com/windowsxp/default.mspx Description: Microsoft Windows XP SP2 Tool Name: MD5 Price: Free Link to Resource: http://www.fourmilab.ch/md5/ Description: From the MD5 site: This page describes md5, a command line utility
usable on either UNIX or MS-DOS/Windows, which generates and verifies message
digests (digital signatures) using the MD5 algorithm. This program can be
useful when developing shell scripts or Perl programs for software
installation, file comparison, and detection of file corruption and tampering. Tool Name:
SAV Corporate
Edition 8.1 Price: $$$$ Link to Resource:
http://www.symantec.com/downloads/ Description: SAV Corporate Edition 8.1 Virus Definitions Tool Name:
Strings Price: Free Link to Resource: http://www.sysinternals.com/Utilities/Strings.html Description: From the Sysinternals site: Working on NT and Win2K means
that executables and object files will many times have embedded UNICODE
strings that you cannot easily see with a standard ASCII strings or grep
programs. So we decided to roll our own. Strings just scans the file you pass
it for UNICODE (or ASCII) strings of a default length of 3 or more UNICODE
(or ASCII) characters. Note that it works under Windows 95 as well. Tool Name:
Hex Workshop Price: Shareware Link to Resource: http://www.hexworkshop.com/ Description: From the Hex Workshop site: The Hex Workshop Hex Editor is a set of hexadecimal
development tools for Microsoft Windows, combining advanced binary editing
with the ease and flexibility of a word processor. With Hex Workshop you can
edit, cut, copy, paste, insert, and delete hex, print customizable hex dumps,
and export to RTF or HTML for publishing. Additionally you can goto, find,
replace, compare, calculate checksums, add smart bookmarks, color map, and
generate character distributions within a sector or file. Hex Workshop supports drag and drop and is integrated
with the Windows operating system so you can quickly and easily hex edit from
your most frequently used workspaces. The Data Inspector is perfect for
interpreting, viewing, and editing decimal and binary values. Arithmetic,
logical, ASCII case, and bitwise operations can be used to help manipulation
your data in place. Tool Name: WinRAR Price: Shareware Link to Resource: http://www.rarlab.com/ Description: From
the WinRAR site: WinRAR is a 32-bit Windows version of RAR Archiver, an
archiver and archive manager. RAR files can usually compress content by 8
percent to 15 percent more than ZIP files can. WinRAR's main features include
strong general and multimedia compression, the ability to process non-RAR
archive formats, ZIP compression and decompression, support for long
filenames, programmable self-extracting archives (SFX), repair of damaged
archives, authenticity verification, embedded file comments, and encryption.
Unicode is supported in archive filenames, allowing non-English filenames to
be handled painlessly. You can manipulate the parameters of many archives at
once and view a volume sequence as a single archive. WinRAR can convert other
archive formats to RAR and search for specified text and files in archives. Tool Name: UPX Price: Free Link to Resource: http://upx.sourceforge.net/ Description: From the UPX site: Ultimate Packer for Xecutables (UPX) is an
extendable software high-performance executable file compression packer for a
number of diverse executable file formats. It achieves an excellent file
compression ratio and fast running decompression. The UPX executables suffer
no memory overhead or negatives. An audit of compressed and uncompressed
files is maintained. UPX is a free, portable, extendable, high-performance
executable packer for several different executable formats. It achieves an excellent
compression ratio and offers very fast decompression. Your
executables suffer no memory overhead or other drawbacks because of in-place
decompression. Tool Name:
Open Watcom
C/C++ Compiler Price: Free Link to Resource: http://www.openwatcom.org/ Description: From Open Watcom’s site: Open Watcom is a joint effort
between SciTech Software
Inc, Sybase®,
and the Open Source development community to maintain and enhance the Sybase
Watcom C/C++ and Fortran compiler products. Plans for Open Watcom include
porting the compiler to the Linux and FreeBSD platforms, as well as updating
the compilers to support the latest C and C++ ANSI standards. Latest Release: Tool Name:
Dumpbin.exe Price: Comes with MS Visual Studio packages Link to Resource: Description: From knowledge base article 177429: The DUMPBIN utility, which is provided with the 32-bit
version of Microsoft Visual C++, combines the abilities of the LINK, LIB, and
EXEHDR utilities. The combination of these tools features the ability to
provide information about the format and symbols provided in executable,
library, and DLL files. Tool Name: PEView Price: Free Link to Resource: http://www.magma.ca/~wjr/ http://www.magma.ca/~wjr/PEview.zip Description: From the PEView site: Quick and easy way to view the structure and content of 32-bit Portable Executable (PE) and Component Object File Format (COFF) files which supports the viewing of EXE, DLL, OBJ, LIB, DBG, and other file types. Tool Name: PEBrowse Professional Price: Free Link to Resource: http://www.smidgeonsoft.prohosting.com/pebrowse-pro-interactive-debugger.html Description: From the PEBrowse Professional site: PEBrowse Professional Interactive builds upon the framework presented by PEBrowse Professional to create a very powerful, versatile, and customizable Win32 user mode debugger/disassembler. PEBrowse Interactive is not a source code debugger, but operates at the Intel x86 instruction level and therefore at the lowest level where your program executes. The debugger fully supports Microsoft .NET managed processes and seamlessly allows interop or mixed-mode debugging. It can be set as the startup debugger using the system registry Image File Execution Options key - useful for debugging ASP.NET applications. Tool Name: OllyDbg Price: Free Link to Resource: http://www.ollydbg.de/ Description: From the OllyDbg site: OllyDbg is a 32-bit assembler level analyzing debugger
for Microsoft Windows. Emphasis on binary code analysis makes it particularly
useful in cases where source is unavailable. OllyDbg is a shareware, but you
can download and use it for free. Additional Resources Books
Reversing: Secrets of
Reverse Engineering By: Eldad Eilam ISBN: 0764574817
Hacker Disassembling Uncovered By: Kris Kaspersky ISBN: 1931769222
By: Kris Kaspersky ISBN: 1931769400
The Art of Computer Virus Research and Defense
Web Resources
PE File Infection Techniques http://rozinov.sfs.poly.edu/presentations/pe_file_infection_techniques_part_1.pdf By: Konstantin Rozinov
|